By Mitchell Hurd & Ashish Shah, Solution Architects
Our annual User Tech Forum featured Dasher solution architects dissecting the volume and intensity of cyber threats as massive security breaches continue to dominate the headlines. With cybercrime damage costs estimated to hit $6 trillion annually by 2021, a IT security awareness, visibility, and best practices for protecting digital assets are essential. We polled 150+ IT professionals with various security-related questions during the forum, and some of their responses were truly surprising:
Question: Which of these statements about cyber attacks in 2017 do you believe is false?
- 25% of cyberattacks involved internal actors
- 66% of malware was installed via email attachments
- 27% of breaches were discovered by third parties
- 81% of breaches leveraged stolen or weak passwords
- 18% of breaches were conducted by state actors
- 8% of breaches involved physical access
- 43% of breaches were via social attacks
The results:
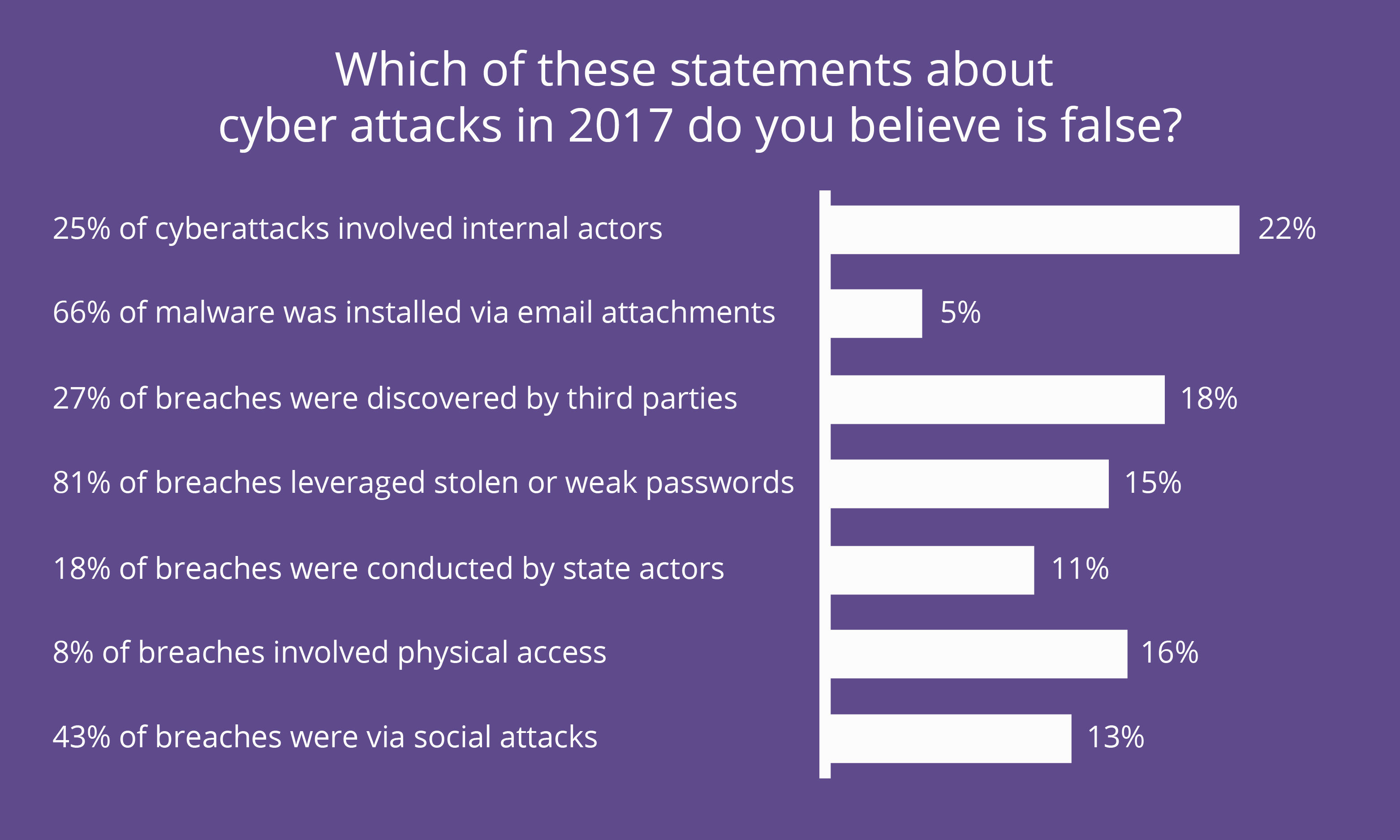
This was a trick question: All statements are true and drawn from the Verizon Data Breach Investigation Report of 2017, illustrating just how pervasive cybersecurity threats are and how vigilant we must be in maintaining awareness. Training new IT professionals on security issues must be a priority in every organization.
The Security Journey
Other questions in the poll were much less tricky, simply seeking to gauge where organizations stand in terms of IT security prioritization.
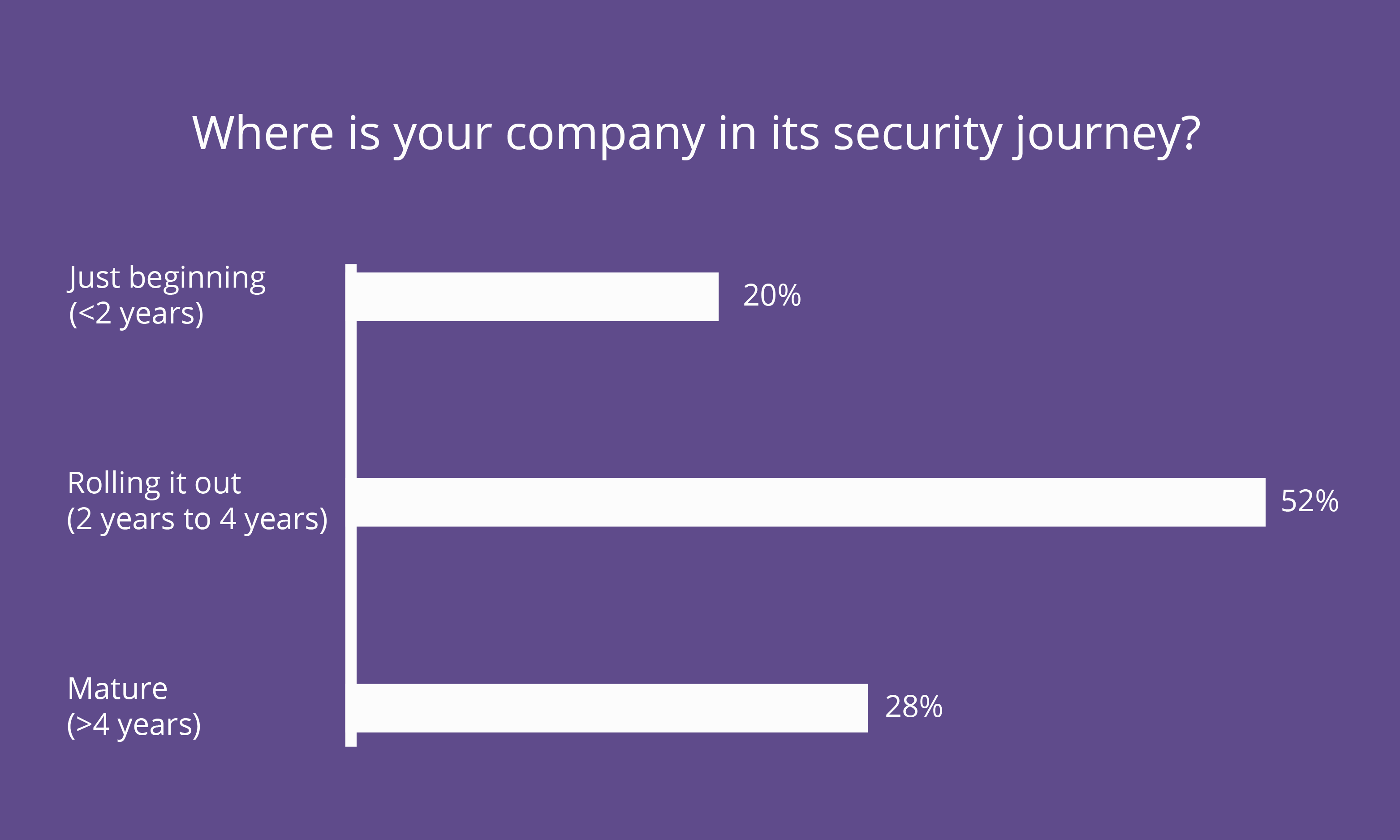
We asked where companies stood in terms of a “security journey.” A majority of the audience just started their security journey or has been building security infrastructure for two to four years. The responses are surprising. Considering the biggest data breaches date back to 2006 — nearly 12 years ago — you’d be forgiven for assuming mature IT security would be more established.
Internet of Things and Network Security
The installed base of IoT devices is forecast to grow to 31 billion worldwide by 2020 and soar to 75.4 billion by 2025, according to industry estimates. There is no one-size-fits-all security architecture and there is a smorgasbord of IoT options: many Dasher clients are using Apple TV or Google Chromecast devices in conference rooms, and Nest thermostats to regulate building temperatures.
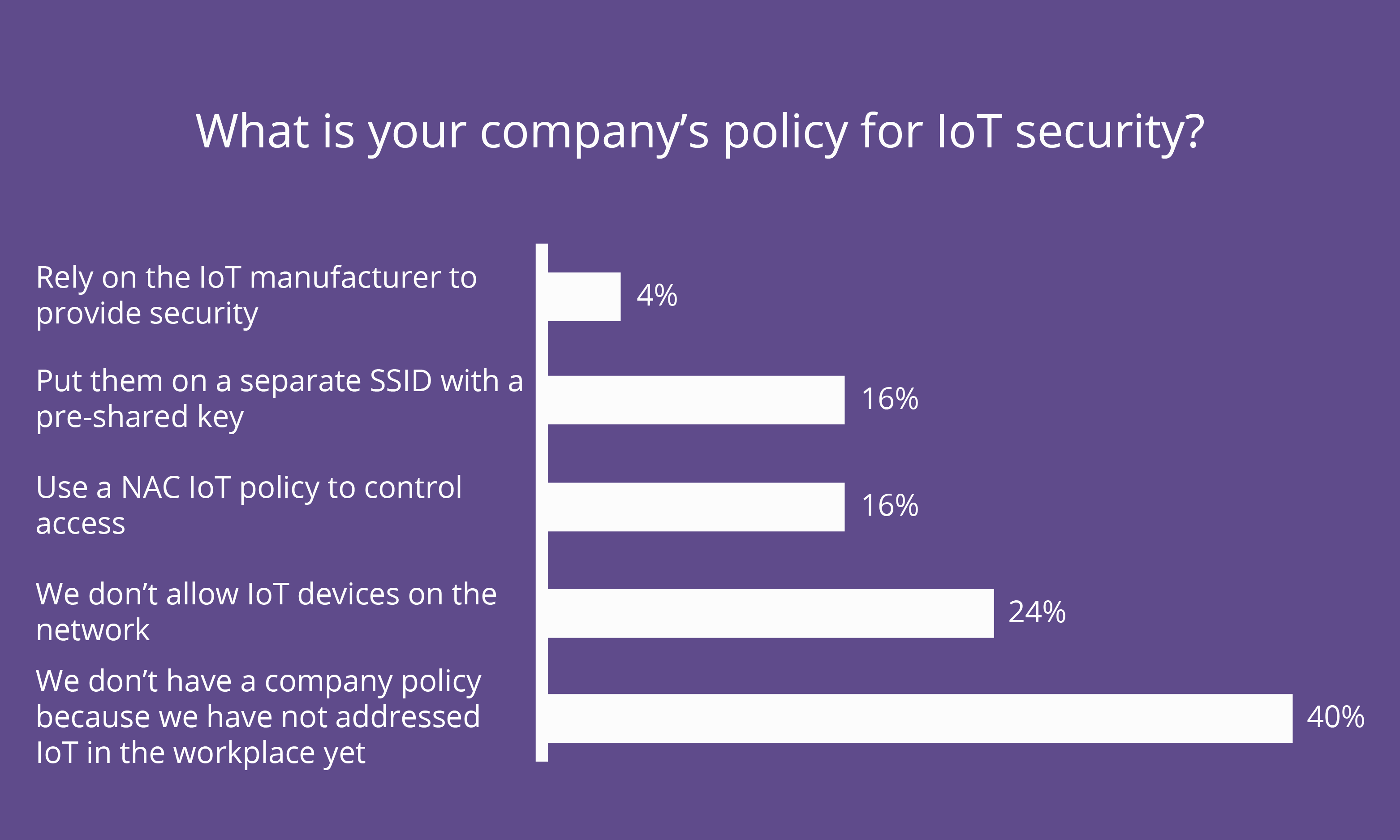
With these connected devices deployed in corporate environments, are IT professionals thinking about security risks and implementing basic controls? Have they created separate wireless networks for IoT devices? We asked. As you can see below, not many companies have policies for IoT devices — yet!
Security-by-Design Mentality
Maintaining IT security is an ongoing responsibility that requires adaptive decision making and constant reflection on ways to improve. We even developed a “Hierarchy of IT Security Needs” to guide that process (you can read about it here [link to Blog#1). We based our User Tech Forum security discussion on a set of cyber practices developed by experts around the world to stop today’s most pervasive and dangerous cyberattacks, the CIS 20 Critical Security Controls, and designed our IT professional poll questions to both engage our partners and inform our team.
Securing the information systems that keep your organization running is an ongoing endeavor that needs to evolve over time in response to trends in the threat landscape. As IT systems grow in scale and complexity, new cyber risks arise and must be countered. Dasher will be there with you to meet those challenges.

