by Kellen Christensen, Solution Architect
According to the world’s most well-known motivation theory, human action is driven to achieve subsistence first (food and shelter), and progresses up a “needs pyramid” through essentials like safety and love to reach actualization or full-potential.
At the recent IT infrastructure conference INTERFACE-Portland, we used Maslow’s pyramid to frame Dasher’s Hierarchy of IT Security needs, showing how to identify and prioritize which layers of security need investment within organizations. A basic breakdown follows this logic (moving from a base subsistence level up to the apex of full potential):
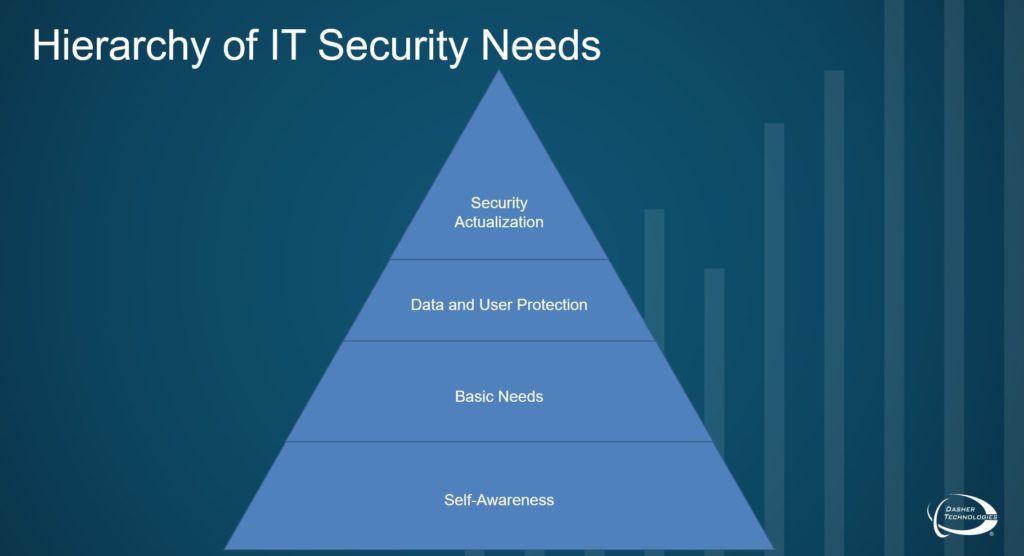
- Self-Awareness: This stage involves determining where you are and where you want to be. It might simply be an IT laundry list of what you have and what you want: firewall, location details on all my users, things you can’t yet afford but would be nice to have, etc. This inventory and/wish list can help guide your strategy into the future.
- Basic Needs: This is where a lot of us really start (skipping self-awareness entirely): antimalware, intrusion detection systems, email security, Wi-Fi security. But truly elemental security practices begin with knowing what and who is on your network, questioning what is being accessed and why. Essentially, visibility is key to the basic need of understanding your risk.
- Data and User Protection: If you have visibility into your network, you can address more sophisticated data and user protections and incorporate broader IT security awareness into your organization’s operations structure: but you have to know who and what you’re trying to protect first.
- Security Actualization: In reality, we never get here. No IT system is ever 100% secure. But if we adequately address all the stages in our needs pyramid, we can reach 99% of our IT security potential.
Coincidentally, just weeks after the INTERFACE conference, CIS released new V7 controls and added three categories it calls “Basic, Foundational, and Organizational” controls. Dasher’s Hierarchy of IT Security Needs intuitively foreshadowed these new CIS categories. Security-obsessed minds think alike — see for yourself:

If you’d like to watch the INTERFACE-Portland session (edited for length), the video is available below.

